Assess Risk exposure/Address Weakness
Emerging Technologies Security Assurance
Identify and mitigate novel vulnerabilities in new systems, devices, and services.

Secure Your Products Before They Enter the Market
New and emerging technologies provide new opportunities to threat actors, broadening the attack surface and introducing new vulnerabilities which require innovative defenses.
This Service Group offers:
Design and Requirements Development- Our experts review your design in detail for potential vulnerabilities and provide guidance for integrating robust security into your design and processes.
Security Assurance Testing
- By combining knowledge gained from our extensive experience and applied research, we develop detailed threat models. These models drive the test plans used to thoroughly evaluate your solution's security profile and levels of risk.
- Launch with peace of mind. Our holistic analysis and testing, based on robust frameworks, cover vulnerabilities and attack vectors across hardware, firmware, software, and protocols.
Reduced Lifecycle Design Costs
- Proactive security design is cost-effective. Anticipating and mitigating vulnerabilities up-front saves you from costly redesign efforts later.
Minimized Service & Deployment Costs
- Leverage our experienced team instead of incurring internal hiring costs. Preventative security saves money compared to the losses (financial and reputational) resulting from successful attacks.
Enhanced Customer Satisfaction
- Secure products and services build trust and loyalty, leading to repeat business and referrals.
- Our diverse team, with broad expertise across information technologies, works closely with you for optimal results.
- Our commitment to applied research keeps us at the forefront of vulnerability awareness. We stay updated on new products and engage with leading industry standards bodies, including IEEE, GSMA, CTIA, and CSA.
- We have extensive experience securing deployments of evolving technologies, including IMS, 4G/LTE, 5G, VoIP, VoLTE, V2X, heterogeneous networks, and Passwordless Identity Management.
- Our "bottom-up" analysis proactively identifies potential vulnerabilities and recommends secure-by-design solutions to mitigate them.
- We provide detailed reports outlining actions taken for reproducibility, detailed results, recommendations for addressing vulnerabilities, and suggestions for improving your security posture.
Services
-
Design & Requirements Development
Our highly-experienced team collaborates on your design from the specification level to the final product, to assure that Secure-by-Design (SbD) principles are being followed.
SbD principles embody a proactive approach to cybersecurity, emphasizing the integration of security measures into the very foundation of software and system development. At its core, this approach prioritizes security considerations throughout the entire lifecycle of a product, from design and implementation to deployment and maintenance. By embedding security features and protocols from the outset, SbD aims to mitigate vulnerabilities and reduce the risk of exploitation by malicious actors. This proactive stance fosters a culture of security consciousness, promoting resilience and trust in digital environments. Key aspects include threat modeling, least privilege access, encryption, secure coding practices, and continuous monitoring, ensuring that security remains a fundamental pillar in your development of emerging technologies products and solutions.
-
Security Assurance Testing
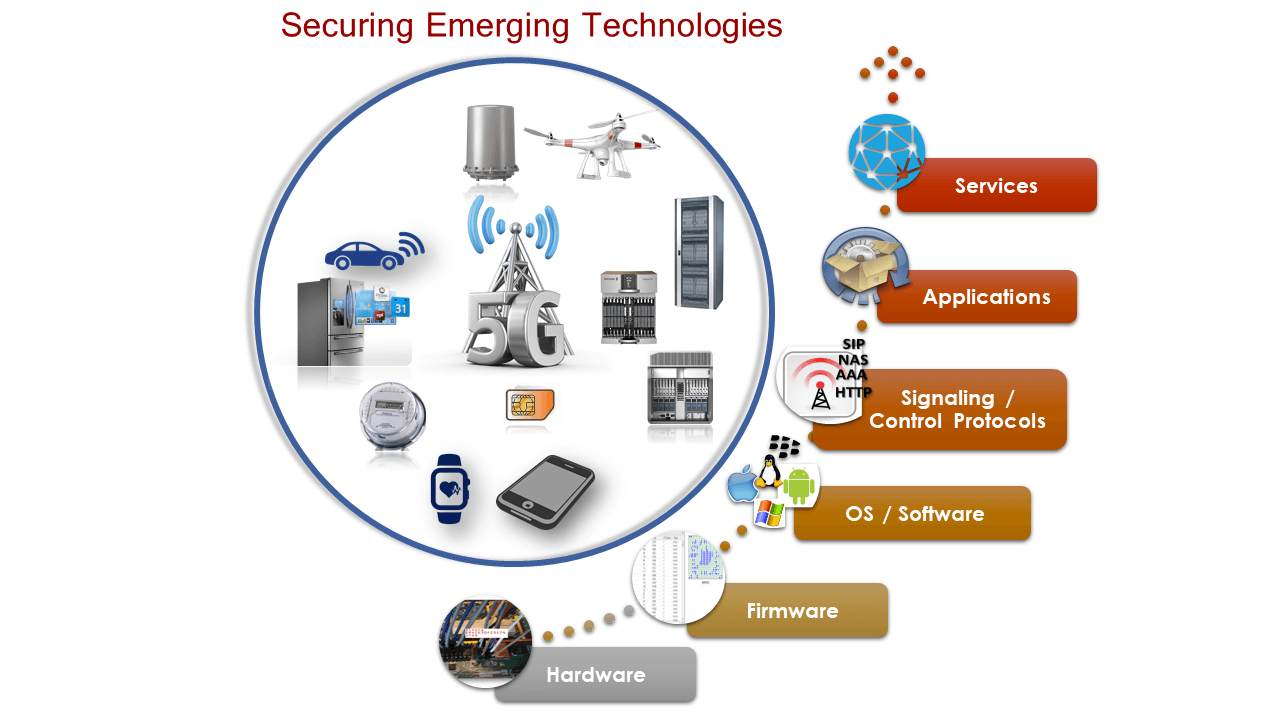
Next-generation devices, including smart phones, medical devices, smart meters and cars, introduce new attack vectors. These devices must maintain security properties that assure confidentiality, integrity and availability. Our extensive experience with product vendors, network operators and application providers ensures that products, applications and services align with industry standards and best security practices. We perform complete life-cycle security assurance evaluation of emerging products and services.
The modular security assurance process framework focuses on specific areas such as SaaS implementations, hardware, mobile applications, provisioning and management systems. It is designed for evaluating products using a multi-dimensional approach that includes security verification of Hardware, Firmware, Software, Signaling and Control Protocols and Applications or Services.




